The Keys for Protecting Your Automation Information
When deciding how to get automation information out of your industrial system, “delivering information” and “connecting to your information” might seem the same. But their vast differences in ability to protect against cyber threats show that one is like a locked door and the other is like no door at all.

Glossary of Terms
Here are some terms and acronyms that will be mentioned frequently in this post:
- Plant automation platform – the combination of PLCs, SCADA, Historians, and dedicated network switches and routers make up a dedicated network
- OT (Operation Technology) – Plant automation platform dedicated network
- PLC (Programmable Logic Controller) – brains of the process controls
- SCADA (Supervisory Control and Data Acquisition) – Communicates with PLC network for visualization, supervisory control like setpoint changes, and data storage
- IT (Information Technology) – Administrative network (office computers, email, printers, phones, cameras, etc.)
- DMZ (Demilitarized Zone) – internal network meets an untrusted network such as the Internet – or the zone in between these two, even through a firewall.
Are There Any Similarities?
The biggest similarity between connecting to your information and delivering information is that both methods get your automation information out of your industrial system.
Then What Are the Differences?
Connecting to your information is an approach to networking your plant automation that leaves it open to security and privacy vulnerabilities. Delivering your information is an approach to networking your plant automation that uses various methods at every level to limit security and privacy vulnerabilities. A cyber attack on your industrial system and users can be automated and happen in a matter of seconds. So it is crucial to be prepared. Each approach has its own offering of equipment and connections.
Connecting to Your Information
When you connect to your information, you make a remote connection that directly interfaces with the OT network, which includes your SCADA system and/or plant automation devices. Methods include: VPN (Virtual Private Network), remote access software like TeamViewer, GoToMyPC, etc. If you have any kind of direct connection, you have a vulnerability. This may give hackers access to your entire plant automation system! If you can get to it, so can someone else.
Even if you are connecting your information indirectly to a single SCADA component that you think is connected but isolated from the OT network, it may not be. Additionally, very few require Multi Factor Authentication and end-to-end encryption like SSL (Secure Sockets Layer). This makes your plant automation system vulnerable.
Once connected to the network, access to everything on the network gets much easier – for you and hackers.
Methods
- VPN (virtual private network)
- Cloud-Based Remote Access (includes LogMeIn, GoToMyPC, and TeamViewer)
- Local Web Server
Vulnerabilities
- inbound port on firewall open/forward
- username and password authentication
- No multi-factor authentication
- No SSL or encryption
- all web traffic is directed to SCADA, or all VPN traffic is directed to SCADA
- control network tied to firewall
- administration network same as control
- public static IP or dynamic DNS
- directly connected to SCADA component
Delivering Information
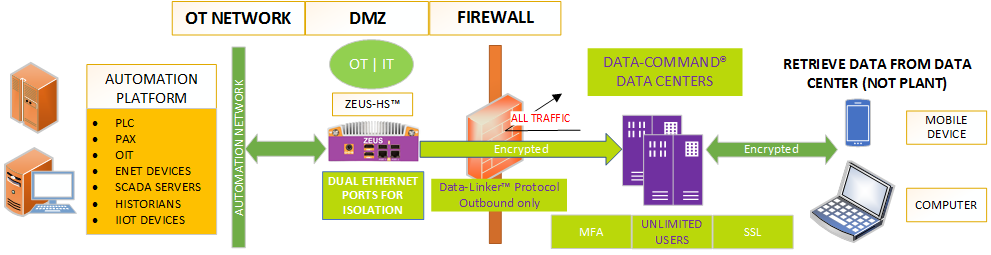
By delivering your information, we are referencing a hardware appliance, specifically designed to live in the DMZ, which is setup to thwart attacks from the untrusted network. It creates a barrier both physically and logically between secured (OT) and untrusted (Internet) networks. Communication to the OT network is handled through the native protocol, however this information is then recompiled into a new proprietary protocol, the packet is then encrypted, and sent to a secure cloud based provider. There is no logical network connection between the secure and unsecure network.
By delivering information and not connecting to the network, your vulnerabilities are almost eliminated.
Methods
- Specialized hardware and software that lives in the DMZ
- End-to-end encryption of data packets
- Cloud-Based Service, which handles MFA, SSL, and other security requirements
Vulnerabilities
Limited
Suggestions for More Secure Remote Access to OT Information
- DON’T: Connect IT and OT networks physically and/or logically – EVER!
- DO: Separate IT from OT network, then create a DMZ for the OT network. Divide the firewall functions into two separate zones. One zone is for the OT and one zone is for the IT.
For more suggestions, download our free white paper!
You wouldn’t take the front door off of your house, opening it up to intruders. Make sure you deliver information, so you don’t expose the automation information of your industrial system.
About The Author
The President and founder of Data-Command with over 25+ years of business development, 35+ years of automation, and 40+ years of software development experience. In 2005, Data-Command was born from his passion to provide information to municipalities and industry that would have a positive impact on their operations, and he has never lost this passion.